Bringing Your Own Encryption Key into AlphaSense AWS
Objective: Enable customers to create and manage their own Customer Master Key (CMK) in AWS Key Management Service (KMS) to use with AlphaSense services.
Prerequisites
- Active AWS account.
- Familiarity with AWS KMS and IAM (Identity and Access Management).
Workflow Diagram
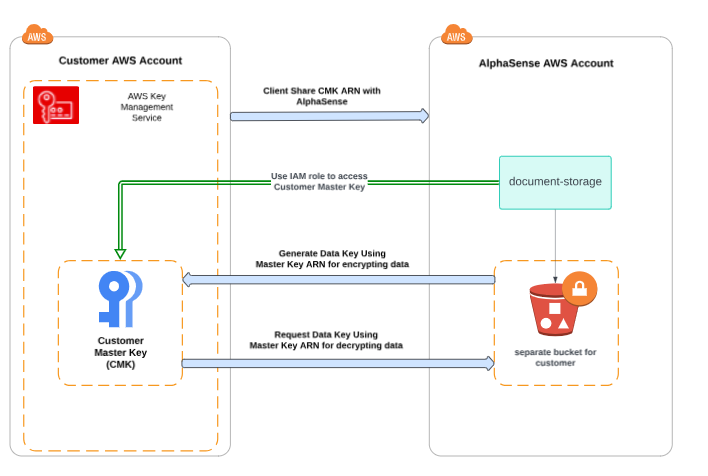
Detailed Steps
1. Create a Customer Master Key (CMK)
- Log in to your AWS Management Console.
- Select region us-east-1
- Navigate to Key Management Service.
- Click on “Create a key”.
- Select “Symmetric” as the key type for general-purpose encryption.
- Select “Encrypt & decrypt“ as the key usage.
- Provide a name and description for the key to identify its use with AlphaSense.
- Configure key administrative permissions: Specify which IAM roles or users can manage the key.
- Configure key usage permissions: Define which accounts, IAM roles, or users can use the key to encrypt and decrypt data. This is not required if AlphaSense is only user of the key.
2. Configure Key Access Policies
Option A: Direct IAM Role Access
- AlphaSense will provide a JSON policy. This should specify the permissions for the service to use the CMK.
- Attach this statement to your CMK key policy to allow AlphaSense to use the keys for encryption.
Example statement:
{
"Sid": "Allow access for AlphaSense",
"Effect": "Allow",
"Principal": {"AWS": "arn:aws:iam::[AlphaSense-Account-ID]:role/[customer-facing-role-name]"},
"Action": [
"kms:Encrypt",
"kms:Decrypt",
"kms:ReEncrypt*",
"kms:GenerateDataKey*",
"kms:DescribeKey"
],
"Resource": "*"
}
AlphaSense will provide the role ARN when needed.
Option B: Assume Role Configuration
For enhanced security and better access control, you can configure an IAM role in your account that AlphaSense can assume to access your KMS key.
Follow the detailed setup guide: IAM Trust Policies and Permissions Guide
Key steps summary:
- Create a client IAM role with trust policy allowing AlphaSense's document-storage-role
- Attach KMS permissions to your client role
- Update your KMS key policy to allow access from your client role
Required permissions for your client role:
- KMS:
Encrypt,Decrypt,ReEncrypt*,GenerateDataKey*,DescribeKey
3. Provide Configuration to AlphaSense
For Direct IAM Role Access (Option A):
- Securely transmit the ARN of your CMK to AlphaSense. Ensure that this communication is done through secure channels.
For Assume Role Configuration (Option B):
- Provide the following information to AlphaSense securely:
- CMK ARN and Region
- Client IAM Role ARN (the role created in your account)
- External ID used in the trust policy
AlphaSense will configure the system to use the chained assume role pattern where the document-storage-role assumes your client role to access the KMS key.
4. Security Considerations
- Regularly audit the IAM roles and policies associated with your CMK.
- Use AWS CloudTrail to log and monitor all key usage.