Configuring and Accessing a Client-Owned S3 Bucket Using a CMK
Objective: Configure an AWS S3 bucket for encryption with a customer-managed CMK and set permissions for AlphaSense access.
Prerequisites
- An AWS account with an existing CMK.
- Familiarity with AWS S3 and AWS KMS.
Workflow Diagram
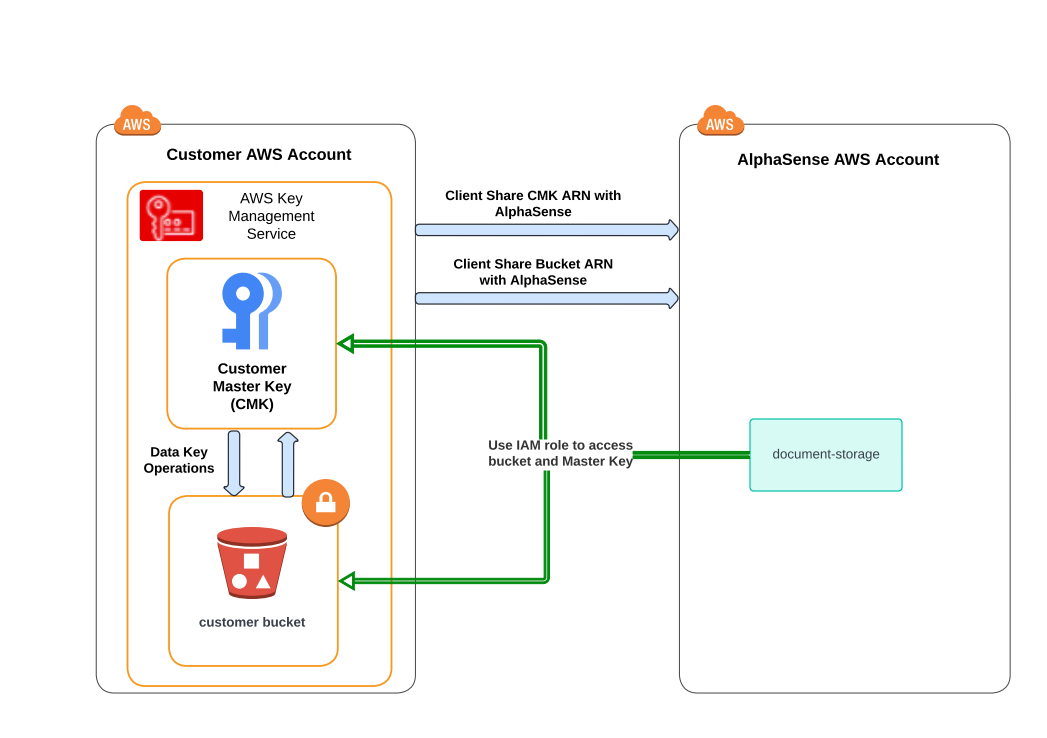
Detailed Steps
1. Create a Customer Master Key (CMK)
- Create Customer Master Key (CMK) and set policies by following steps 1-3 in Bringing Your Own Encryption Key into AlphaSense AWS.
- Take note of the key ARN
2. Select or Create an AWS S3 Bucket
- Navigate to the S3 management console.
- Choose region: you must use same region as for your key
- Create a new bucket or select an existing one to configure for AlphaSense usage
3. Enable Bucket Encryption
Enable encryption in the bucket configuration using your CMK. Use default values for other settings:
- General Configuration
- Bucket type: General purpose
- Object Ownership
- ACLs disabled
- Block Public Access settings for this bucket
- Block all public access
- Bucket Versioning
- disable
- Default encryption
- Server-side encryption with AWS Key Management Service keys (SSE-KMS)
- Select your previously created CMK
4. Configure Bucket and Key Access Policies
Option A: Direct IAM Role Access
- In the Amazon S3 console: select your bucket and go to "Permissions" tab
- Click edit bucket policy
- Example Bucket Policy is listed below. AlphaSense will provide you the exact policy including the complete ARN. The policy will allow AlphaSense system to save, get, list and delete objects in the bucket.
- Saved objects include original customer uploaded files, as well as all derived files that are needed to process and display customer content on AlphaSense system.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {"AWS": "arn:aws:iam::[AlphaSense-Account-ID]:role/[customer-facing-role-name]"},
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:RestoreObject",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": "arn:aws:s3:::[Your-Bucket-Name]/*"
}
]
}
Option B: Assume Role Configuration
For enhanced security and better access control, you can configure an IAM role in your account that AlphaSense can assume to access your bucket and KMS key.
Follow the detailed setup guide: IAM Trust Policies and Permissions Guide
Key steps summary:
- Create a client IAM role with trust policy allowing AlphaSense's document-storage-role
- Attach S3 and KMS permissions to your client role
- Update your S3 bucket policy to allow access from your client role
- Update your KMS key policy to allow access from your client role
Required permissions for your client role:
- S3:
GetObject,PutObject,RestoreObject,ListBucket,DeleteObject - KMS:
Encrypt,Decrypt,ReEncrypt*,GenerateDataKey*,DescribeKey
5. Transmit Configuration to AlphaSense
For Direct IAM Role Access (Option A):
- Provide the ARNs & Region for both the bucket and the CMK to AlphaSense securely.
For Assume Role Configuration (Option B):
- Provide the following information to AlphaSense securely:
- S3 Bucket ARN and Region
- CMK ARN and Region
- Client IAM Role ARN (the role created in your account)
- External ID used in the trust policy
AlphaSense will configure the system to use the chained assume role pattern where the document-storage-role assumes your client role to access the bucket and KMS key.
6. Security Considerations
- Enable bucket logging to monitor access and actions performed.
- Regularly review your security settings and policies to ensure they meet your organization's requirements.